
Za darmo
Wszystkie poziomy
Kurs języka angielskiego Memrise
Wyrażaj swoje myśli po angielsku z pewnością siebie
Rozpocznij kursO kursie
- Wybierz scenariusze, do których chcesz się przygotować i ucz się zawartych w nich słów
- Posłuchaj słów wypowiadanych przez native speakerów
- Ćwicz mówienie na osobności z Twoim partnerem językowym ze sztuczną inteligencją
O kursie
- Wybierz scenariusze, do których chcesz się przygotować i ucz się zawartych w nich słów
- Posłuchaj słów wypowiadanych przez native speakerów
- Ćwicz mówienie na osobności z Twoim partnerem językowym ze sztuczną inteligencją
400+ lekcji
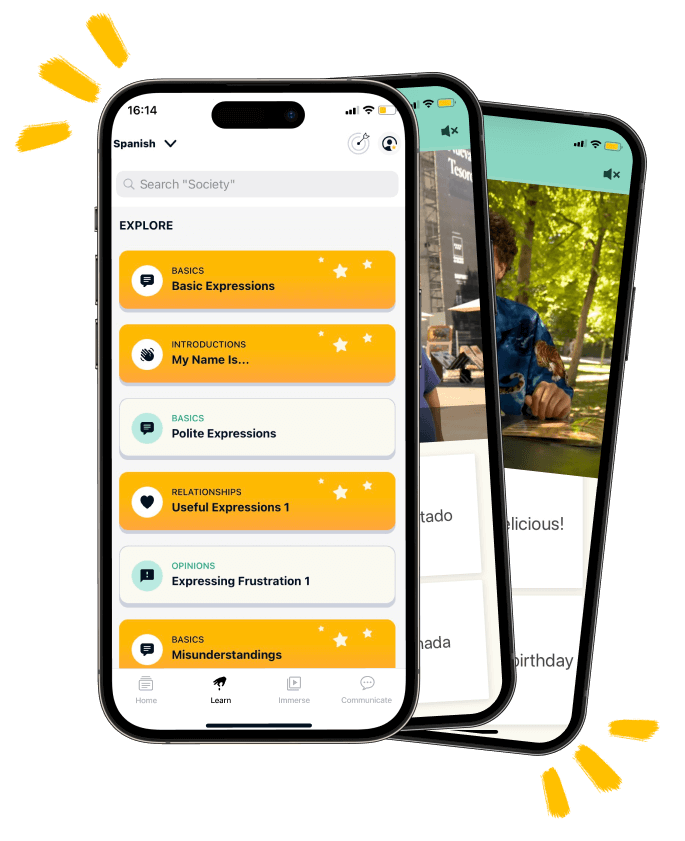
opartych na poniższych tematach. Naucz się angielskich zwrotów, którymi posługują się miejscowi, aby przygotować się do konwersacji.what's up?/co słychać?
4000+ słów
Słowa, których się uczysz, będą wypowiadane przez native speakerów.
what's up?/co słychać?
300+ filmów

Zanurzenie w języku to najszybszy sposób nauki. Oglądaj native speakerów i osłuchaj się z ich akcentami.

75+ konwersacji ze sztuczną inteligencją
Buduj pewność siebie w domowym zaciszu, rozmawiając ze swoim nauczycielem języka ze sztuczną inteligencją.
 Eksperci językowi
Eksperci językowi

 Eksperci językowi
Eksperci językowi
Nasz kurs angielskiego tworzony jest przez doświadczonych językoznawców i opiera się na wieloletnich badaniach naukowych.
Oto, co mówią nasi użytkownicy
- To świetny program do nauki angielskiego
 efe4814
efe4814 - Bardzo przydatna i przyjemna aplikacja dla osób zainteresowanych nauką angielskiego.
 -Nick-Chen
-Nick-Chen - Używałem i oceniłem co najmniej 20 aplikacji językowych, ukończyłem też trzy pełne kursy na Duolingo (brazylijski portugalski, francuski, włoski i trochę hiszpańskiego w ramach uzupełnienia). Memrise jest DUŻO lepsza od pozostałych. Narzędzia do nauki są skuteczne i zróżnicowane. Wszystko jest wyraźnie wymawiane i przetłumaczone na angielski zarówno w dosłowny sposób, jak i normalnie.
 Jpmcftghbmo
Jpmcftghbmo
Recenzje pochodzące z
Dołącz do 364 000 użytkowników, którzy uczą się szybciej dzięki Memrise Premium
- Koniec z reklamami
- Pełny dostęp do wszystkich języków
- 45 000 filmów z native speakerami
Najczęściej Zadawane Pytania (FAQ)
Dlaczego warto uczyć się brytyjskiego angielskiego?
Angielski to jeden z najczęściej używanych języków na świecie, a ponad 380 milionów ludzi używa go jako swojego pierwszego języka. Nauka angielskiego może pomóc Ci w porozumiewaniu się z ludźmi z całego świata - zwłaszcza, jeśli jesteś fanem kultury popularnej. Mnóstwo znanych piosenek, filmów i programów telewizyjnych produkowanych jest w języku angielskim. Znajomość angielskiego może okazać się niezwykle pomocna w Twojej karierze. Wiele firm używa angielskiego jako swojego oficjalnego języka, dlatego umiejętność płynnego posługiwania się nim może zapewnić Ci znaczną przewagę na rynku pracy.
Dlaczego warto uczyć się angielskiego z Memrise?
Memrise pomoże Ci się dogadać po angielsku w najważniejszych dla Ciebie sytuacjach z życia codziennego, np. w podróży, podczas spotkań z rodziną Twojego partnera czy w czasie rozmów z kolegami z pracy.
Wybieraj spośród setek praktycznych scenariuszy, a Memrise dostarczy Ci angielskich słówek i ćwiczeń, które pozwolą Ci opanować konkretne rozmowy w języku angielskim.
- Rozwijaj słownictwo przy pomocy angielskich słówek i zwrotów używanych przez miejscowych.
- Słuchaj native speakerów używających słówek, których się uczysz, aby móc ich zrozumieć w prawdziwym świecie.
- Ćwicz mówienie ze swoim nauczycielem języka ze sztuczną inteligencją i zyskaj pewność siebie bez świadków, jeszcze przed rozpoczęciem prawdziwej rozmowy.
Wybieraj spośród setek praktycznych scenariuszy, a Memrise dostarczy Ci angielskich słówek i ćwiczeń, które pozwolą Ci opanować konkretne rozmowy w języku angielskim.
- Rozwijaj słownictwo przy pomocy angielskich słówek i zwrotów używanych przez miejscowych.
- Słuchaj native speakerów używających słówek, których się uczysz, aby móc ich zrozumieć w prawdziwym świecie.
- Ćwicz mówienie ze swoim nauczycielem języka ze sztuczną inteligencją i zyskaj pewność siebie bez świadków, jeszcze przed rozpoczęciem prawdziwej rozmowy.
Od czego zacząć naukę angielskiego?
Nasi eksperci językowi stworzyli setki praktycznych „scenariuszy”, które możesz wybrać na początku swojej podróży językowej. Scenariusze te odnoszą się do Twoich zainteresowań i powodów, dla których uczysz się angielskiego, niezależnie od tego, czy chodzi o prowadzenie rozmów z rodziną Twojego partnera, czy rozumienie tekstów Twoich ulubionych piosenek.
Wybierz scenariusz i naucz się najistotniejszych angielskich słówek i zwrotów używanych przez miejscowych.
Po opanowaniu kilku przydatnych słów w języku angielskim, możesz przystąpić do ćwiczeń ze słuchania. Zanurz się w filmach z udziałem angielskich native speakerów używających słów, których się uczysz, w kontekstach z życia codziennego. Jest to istotne, ponieważ pozwoli Ci to na rozumienie prowadzonych rozmów.
Następnie przejdziesz do ćwiczeń konwersacyjnych z Twoim nauczycielem języka ze sztuczną inteligencją - będą one nawiązywać do wybranych przez Ciebie scenariuszy. Chcesz zamówić jedzenie w restauracji po angielsku? Ćwicz podobne tematy bez świadków, aby móc śmiało rozmawiać w prawdziwym świecie.
Wybierz scenariusz i naucz się najistotniejszych angielskich słówek i zwrotów używanych przez miejscowych.
Po opanowaniu kilku przydatnych słów w języku angielskim, możesz przystąpić do ćwiczeń ze słuchania. Zanurz się w filmach z udziałem angielskich native speakerów używających słów, których się uczysz, w kontekstach z życia codziennego. Jest to istotne, ponieważ pozwoli Ci to na rozumienie prowadzonych rozmów.
Następnie przejdziesz do ćwiczeń konwersacyjnych z Twoim nauczycielem języka ze sztuczną inteligencją - będą one nawiązywać do wybranych przez Ciebie scenariuszy. Chcesz zamówić jedzenie w restauracji po angielsku? Ćwicz podobne tematy bez świadków, aby móc śmiało rozmawiać w prawdziwym świecie.
Czy lekcje angielskiego będą dostosowane do mojego poziomu zaawansowania?
Tak. Memrise jest dostosowany do wszystkich poziomów znajomości języka - swój poziom wybierzesz podczas rejestracji.
Wszystkie nasze filmy są też filtrowane pod kątem dopasowania do słówek, których się uczysz!
Memrise spróbuje Cię zmotywować do zrobienia realnych postępów w opanowywaniu scenariuszy, które są niezbędne do prowadzenia udanych rozmów.
Czasami może się to wydawać trudne, ale nie będzie przytłaczające.
Wszystkie nasze filmy są też filtrowane pod kątem dopasowania do słówek, których się uczysz!
Memrise spróbuje Cię zmotywować do zrobienia realnych postępów w opanowywaniu scenariuszy, które są niezbędne do prowadzenia udanych rozmów.
Czasami może się to wydawać trudne, ale nie będzie przytłaczające.
Ile czasu muszę poświęcić na naukę angielskiego?
To zależy od Ciebie.
Sugerujemy regularne wykonywanie niewielkiej ilości ćwiczeń, dlatego przygotowaliśmy dla Ciebie zalecaną ścieżkę nauki. Zawsze możesz uczyć się więcej lub mniej, jeśli tylko chcesz.
Sugerujemy regularne wykonywanie niewielkiej ilości ćwiczeń, dlatego przygotowaliśmy dla Ciebie zalecaną ścieżkę nauki. Zawsze możesz uczyć się więcej lub mniej, jeśli tylko chcesz.
Czy otrzymam certyfikat ukończenia kursu języka angielskiego?
Nasze kursy nie kończą się otrzymaniem certyfikatu.
Jesteśmy jednak pewni, że umiejętność dogadywania się z miejscowymi przysporzy Ci szacunku na dzielnicy!
Jesteśmy jednak pewni, że umiejętność dogadywania się z miejscowymi przysporzy Ci szacunku na dzielnicy!
Czy trudno jest nauczyć się angielskiego?
To wcale nie musi być trudne! Sekret do łatwiejszej i przyjemniejszej nauki jest dość prosty - skup się na nauce tego, czego chcesz się uczyć!
Memrise dostarcza Ci treści opartych na Twoich powodach do nauki angielskiego.
Memrise dostarcza Ci treści opartych na Twoich powodach do nauki angielskiego.
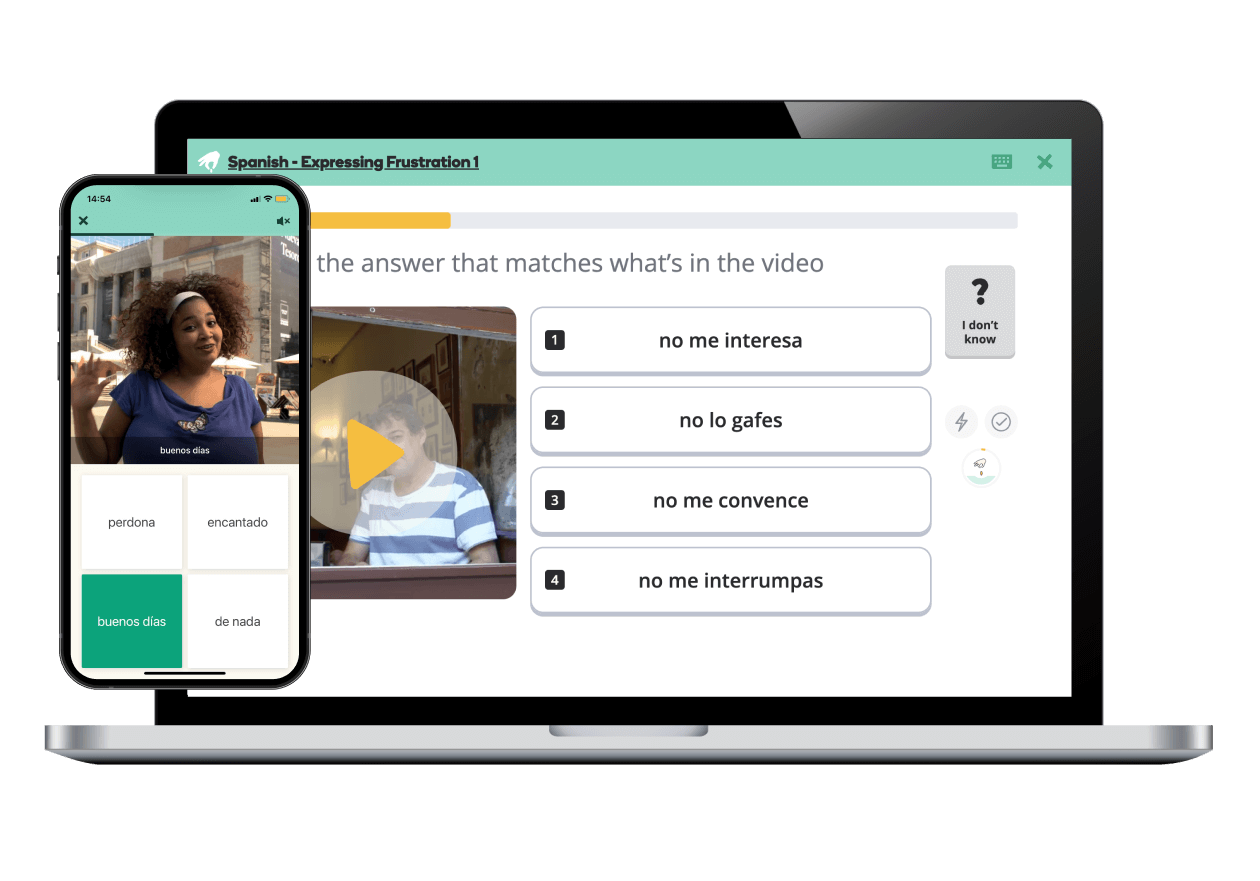
Różne urządzenia
Ciesz się dostępem do wszystkich języków na telefonie i komputerze
Zacznij naukę już terazZacznij naukę
